The key management system consists of a ministerial key system and a city-level key system. The two-level key system generates application keys for different purposes based on different priorities. The key is transmitted between the ministerial key system and the city-level key system by means of a key mother card or a hardware encryption machine. The key management system must have the backup mechanism of the root key and the key emergency update mechanism after the key is leaked. The transfer, copy, and dispersion after the key is generated should generally be performed through an encryption machine or a smart IC card. Keep the key secure.
The key management system is a joint pilot of financial IC cards of commercial banks. The security control and management of keys by banks at all levels is the key to application system security. The key management system adopts the 3DES encryption algorithm, and uses the three-level management system of the People's Bank of China, the People's Bank of China branch (commercial bank head office) and member banks to securely share the public master key to realize card intercommunication and machine sharing. In the joint pilot of financial IC cards of commercial banks, the security control and management of keys by banks at all levels is the key to application system security.
Key management system architectureThe key system is the security foundation and guarantee of the social security (personal) card. Its architecture is multi-layered and the data source is more complicated. Therefore, this part of the software should be able to provide users with transparent services (that is, users do not need to know the specific details and physical addresses of the keys, they can easily use the software to complete the corresponding operations) and can complete the corresponding business functions according to user needs. .
Since the system requires dedicated hardware (encryptors, card readers, etc.), the software should also provide settings and communication operations for these hardware. The specific function division and function requirements of the software are shown in the following figure and description.
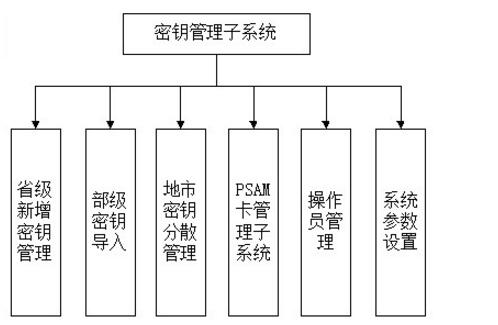
1. Provincial-level new key management: Manage provincial key scatter factors and generate provincial seed key cards.
2. Department-level key import: Read the key provided by the Ministry of Labor and Social Security and import it into the provincial encryption machine.
3. Local city key dispersion: Decentralized national and provincial keys to municipal key systems.
4. PSAM card management: PSAM card data management, PSAM card production.
5. Operator Management: Manage operator data and operator permissions.
6. System parameter setting: Set interface parameters (encryptor address, card issuer connection mode, etc.).
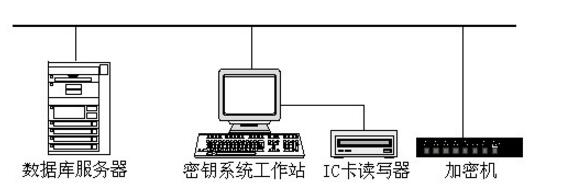
The special necessary hardware involved in the key management system includes: 1 encryption machine (subject to social security regulations) for storing keys; 1 card reader (at least double deck) for reading of user cards or PSAM cards write.
Due to the high security requirements of key management, the key management software should be installed on a dedicated PC to run separately from the rest of the system. In order to back up the key data, the key management software should be equipped with a database such as OraclePersonal or SQLServerDesktop or ACCESS.
1. Any password is not stored in clear text unless it is placed in a secure device. Manually assigned keys must be kept by different trusted entities in the form of key components. They must not be directly controlled by a single entity in plain text. Any operation on the cryptographic device cannot cause the key to appear in clear text. Outside the device;
2, to ensure the separation of the key, different communication entities use different keys, and these keys can not be related, that is, there is a problem in the secure communication between a pair of communication entities, should not cause another pair of entities Secure communication, including the case where two of the four entities are the same;
3, the key needs to have a certain backup mechanism. When the system fails, the key should be lost. It should be able to ensure that the system is repairable by replying to the key backup, but the key backup should not reduce the key management. Security.
4. The key must have a validity period. When the old key expires, the key replacement needs to be performed in time. At the same time, the security of the new key and the security of the old key should be separated, that is, the old key should not be caused even if it leaks. There is a problem with the security of the new key.
5, key management needs to be hierarchical.
The network requires PIN confidentiality for each transaction. The calculation of the MAC and the encryption of other information are different from each other, and are made one time. In order to ensure the continuity of the transaction, these keys are generated by one entity and transmitted securely to another entity communicating with it. This requires the communication parties to jointly use an encryption key (KEK) to encrypt the above. Various work keys, KEK can not be transmitted through the network, but can only be loaded before the system is used, or each of the two entities respectively generates a same key as the KEK. With KEK, the session key is solved. Transmission problem.
In the network, merchants and issuers need to communicate securely with a large number of entities. This requires a large number of keys (session keys and KEK) in the system. These keys cannot be stored in the secure cryptographic device. These keys need to be encrypted and stored in a host database outside the cryptographic device using a Master Key (MFK).
Level 1: MFK, the master key, stored in the key installation, used to encrypt KEK and SK, to be stored in the password.
Level 2: KEK, key encryption key, used for encrypted transmission of SK, each pair of communication entities have the same KEK.
Level 3: SK, session key, used to encrypt PIN, generate MAC and verify MAC.
6, key and key attributes
Both KEK and SK have key attributes for functional separation and use of legality checks to improve the logical security of the system. The attribute of the key contains the level of this key (identification KEK or SK). Use the effective number of .MFK serial numbers. For key usage and key check value, the key attribute is used with the key, and the cryptographic device verifies the validity of the key usage based on the key attribute. Control key misuse. The key check value is generated by the corresponding key value and attribute under the MFK encryption. The key attribute is only stored in the host with the plain text of the corresponding key, and is also used only for the host security crypto device, and is not transmitted.
Introduction to smart card key management systemThe system fully supports the "China Financial IC Card Specification v1.0", specifically:
1. The consumption of electronic wallet and electronic passbook of IC card. Cash out. The balance check function is used nationwide and uses offline trading.
2. The storage of IC cards. The circle is available nationwide, but it is implemented online by means of Longka network.
3. Change the confidentiality of the IC card PIN. Other features such as unlocking are only accepted at the issuing bank.
Smart card key management system features: On the basis of fully guaranteeing the security of the key, the generation of the IC card joint pilot key is supported. Export. injection. Backup. restore. Update. Services such as services to achieve secure management of keys.
Description of Zipper Braided Sleeve
Whether your problem is getting past large connectors or not wanting to disconnect complex cable runs, this zipper cable sleeve side-entry braided wrap is an ideal cable management solution. Zip up cable sleeving is great for wire installations in which only a small portion of the bundle needs to be concealed, and is easily removed and relocated at your convenience.
Our expandable braided zipper sleeving offers exceptional cable protection, but is really used to tidy up exposed cable runs. TV, computer and phone setups can all have a clean and organized cables instead of those ugly cable nests.
Automotive and marine applications such as aftermarket speaker systems, GPS or other component accessories that may need cable organization can benefit from this braided sleeving.
Braided Cable Sleeves,Zip Braided Sleeve For Cable ,Expandable Braided Cable Sleeves,Zipper Cable Sleeves
Shenzhen Huiyunhai Tech.Co.,Ltd , https://www.hyhbraidedsleeve.com